FALCON ENDPOINT
PROTECTION ENTERPRISE
Unifies the technologies required to successfully stop breaches, including true next-gen antivirus and endpoint detection and response (EDR), managed threat hunting, and threat intelligence automation, delivered via a single lightweight agent.
Watch Demo-
FALCON
PREVENTNext-Generation
Antivirus -
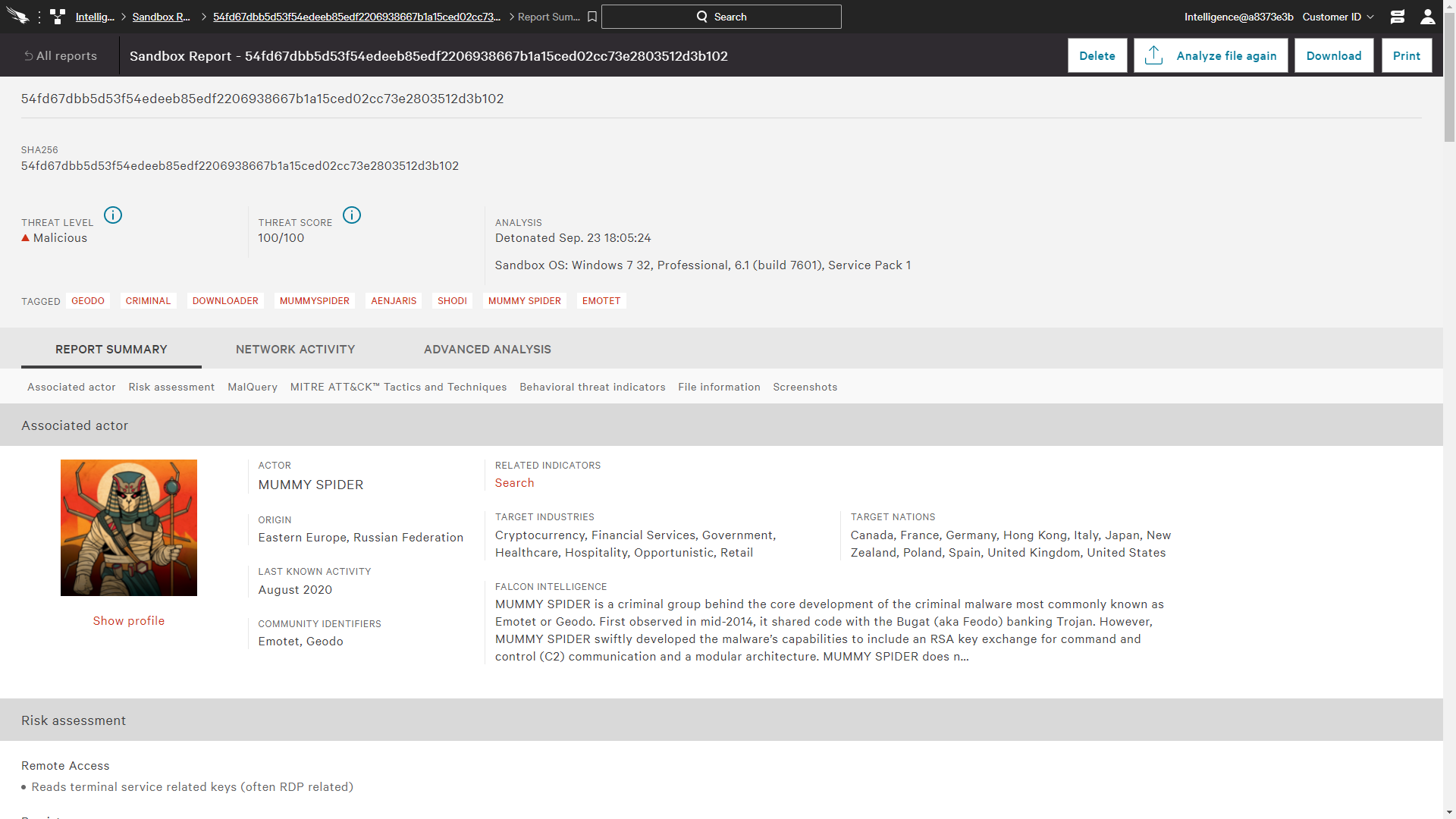
CrowdStrike Falcon® IntelligenceThreat Intelligence
-
FALCON
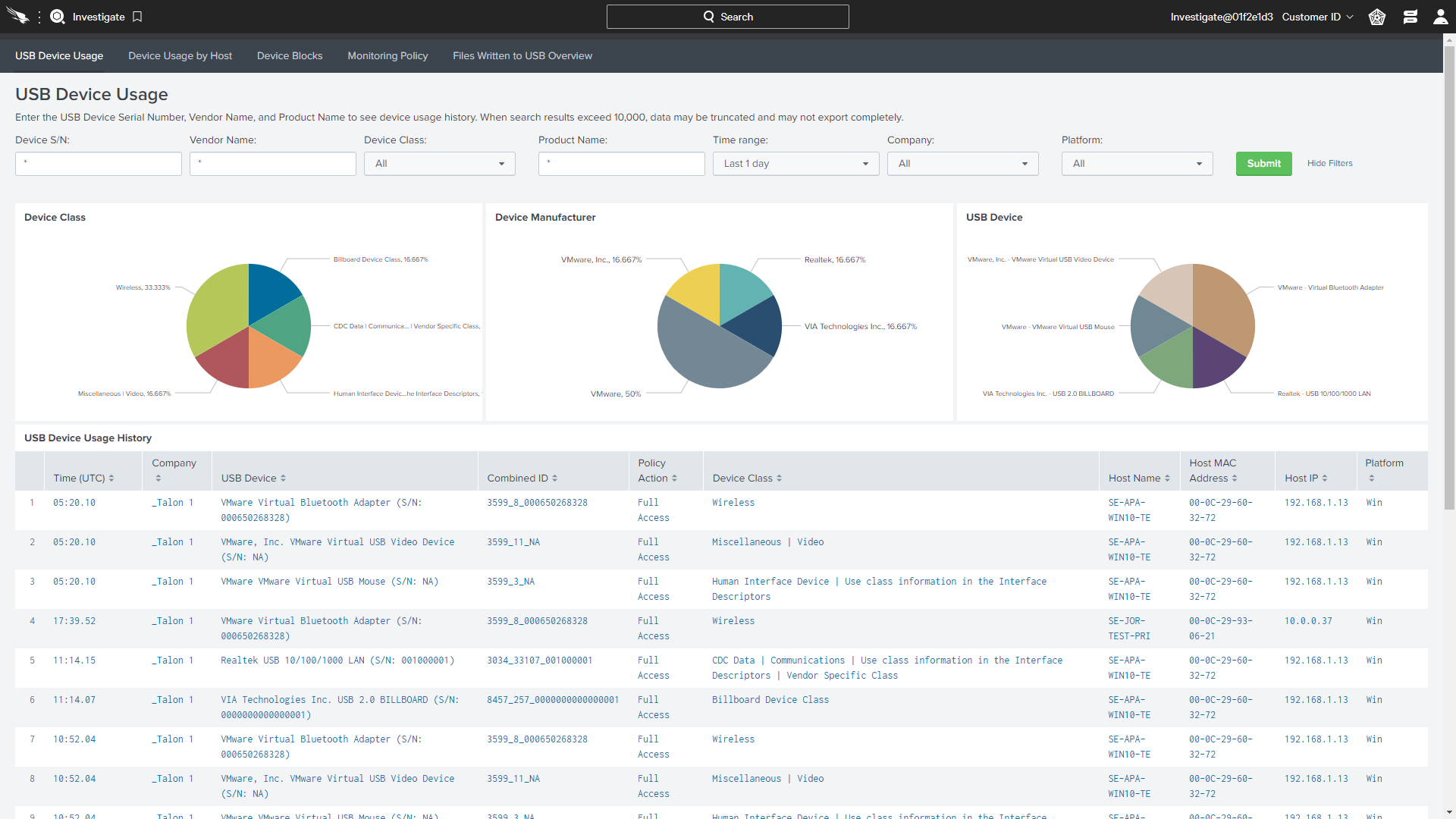
Device ControlUSB Device Control -
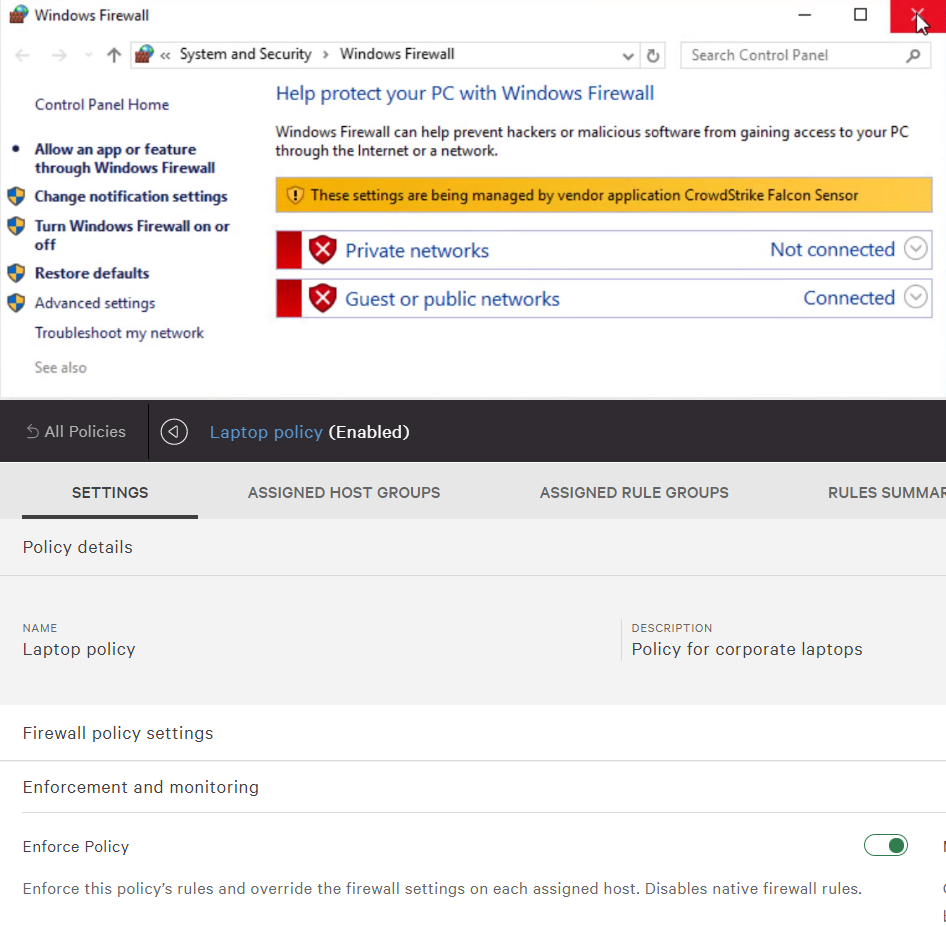
Falcon Firewall Management Host Firewall Control
-
FALCON
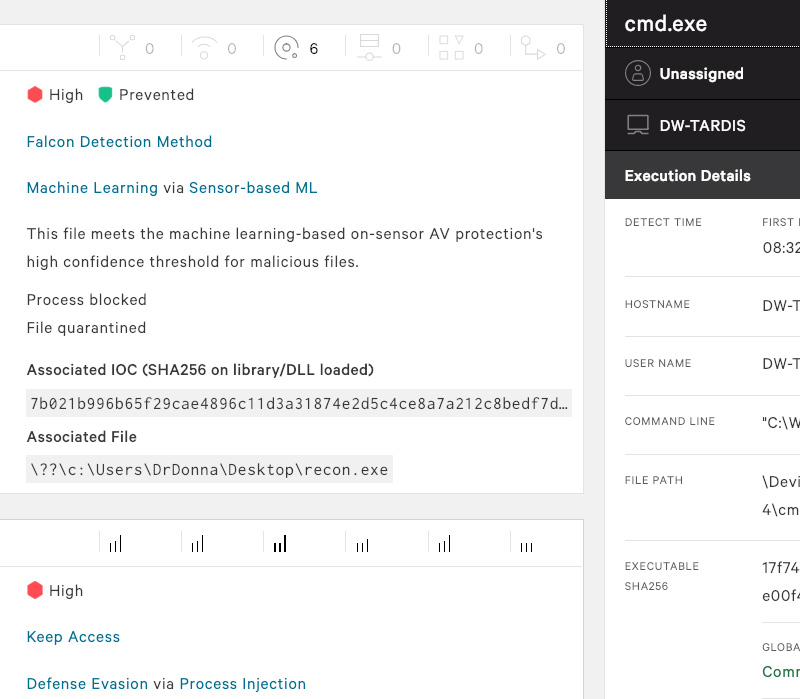
INSIGHTEndpoint Detection
& Response -
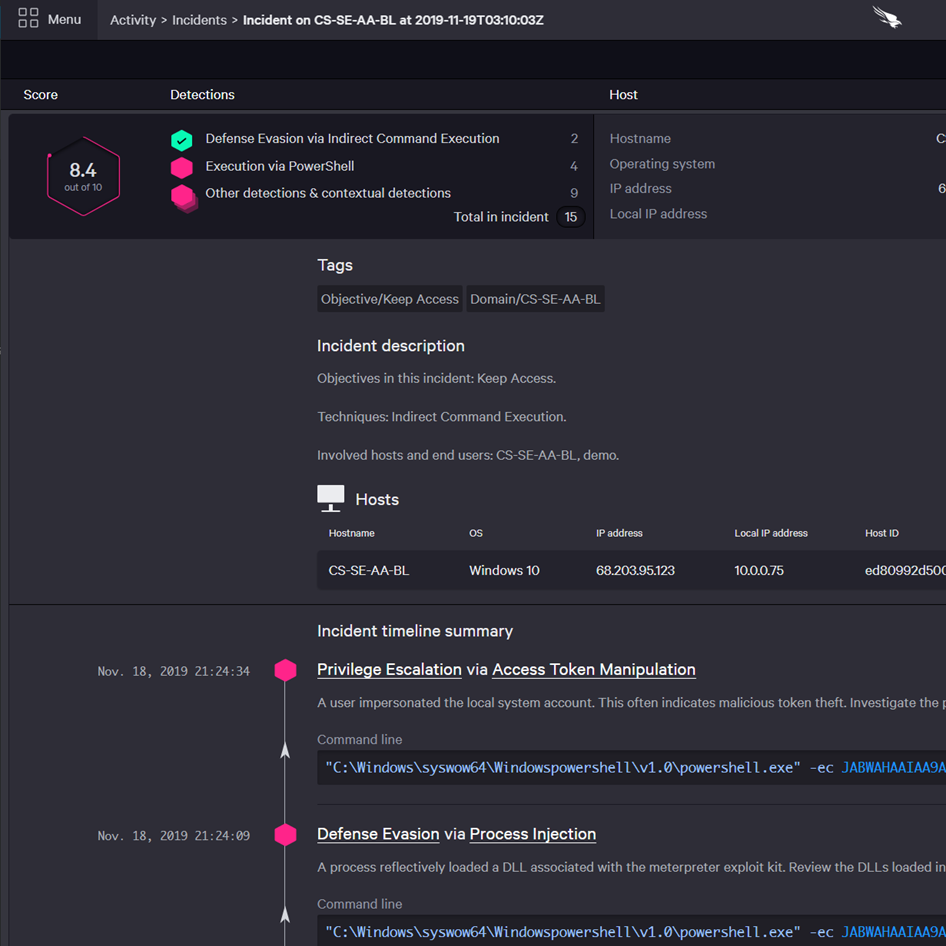
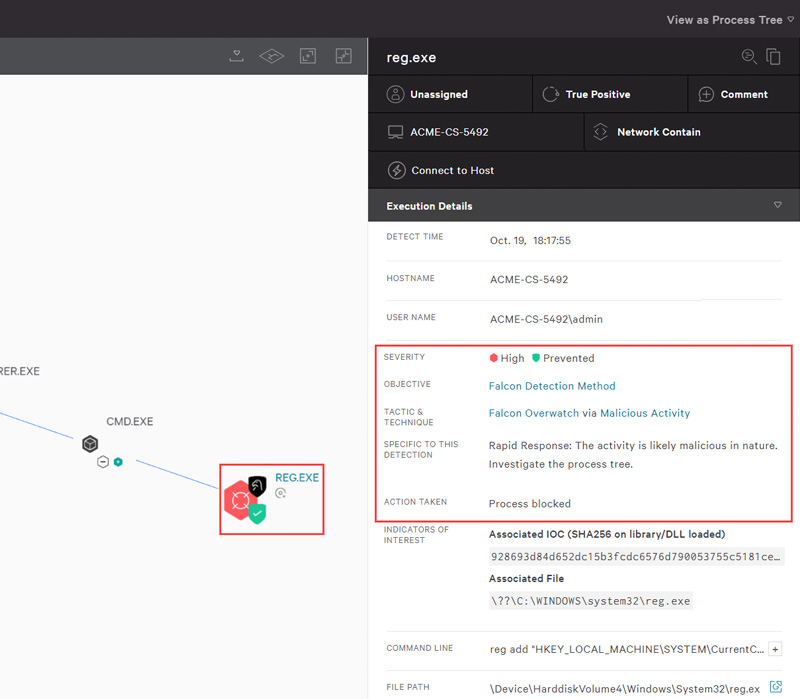
FALCON
OVERWATCHThreat Hunting -
FALCON
DISCOVERIT Hygiene -
FALCON IDENTITY
PROTECTIONIntegrated Identity Security -
CROWDSTRIKE
SERVICESIncident Response &
Proactive Services
- Falcon Enterprise Unified NGAV, EDR, managed threat hunting and integrated threat intelligence
-
Available with
FALCON ELITE -
Available with
FALCON ELITE - Learn more about CrowdStrike Services
Flexible Bundles:
Included Component
Elective Component

Recognized by Gartner Peer Insights CrowdStrike named a Customers’ Choice vendor in the 2021 Gartner Peer Insights Report for EPP. Learn More
REAP THE BENEFITS OF CROWDSTRIKE’S
FALCON ENDPOINT
PROTECTION ENTERPRISE
Sets the new standard with the first cloud-native security platform that delivers the only endpoint breach prevention solution that unifies NGAV, EDR, managed threat hunting and threat intelligence automation in a single cloud-delivered agent.
BUSINESS VALUE
-
Increases Security
Efficiency -
Improves
Productivity -
Decreases Risks
of Breach -
Reduces Time
to Respond
MODULES INCLUDE
INTERESTED?
A CrowdStrike security expert is standing by to offer information, advice, or help with your purchase.
Request Info