FALCON ENDPOINT
PROTECTION PRO
Market-leading NGAV proven to stop malware with integrated threat intelligence and immediate response — with a single lightweight agent that operates without the need for constant signature updates, on-premises management infrastructure or complex integrations, making it fast and easy to replace your AV.
Start free trial-
FALCON
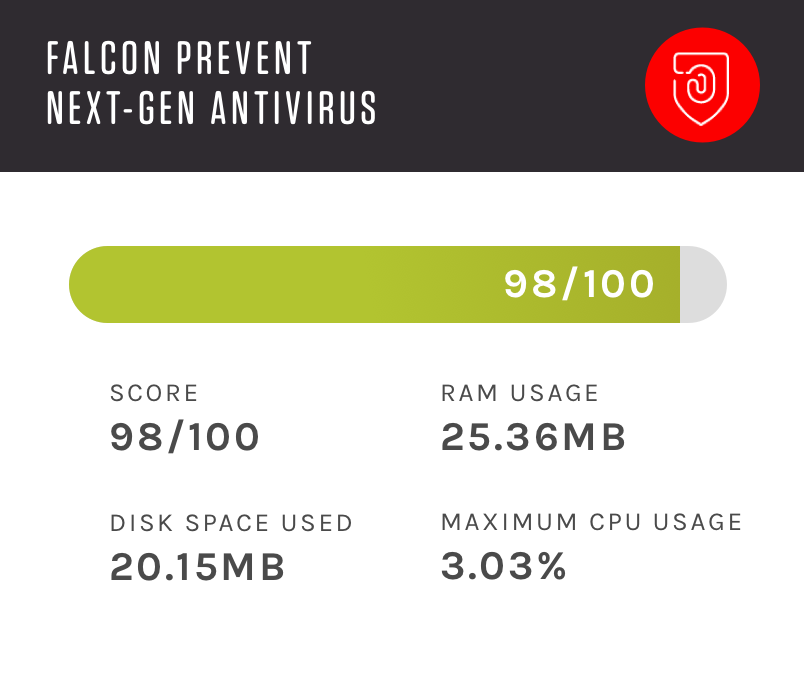
PREVENTNext-Generation
Antivirus -
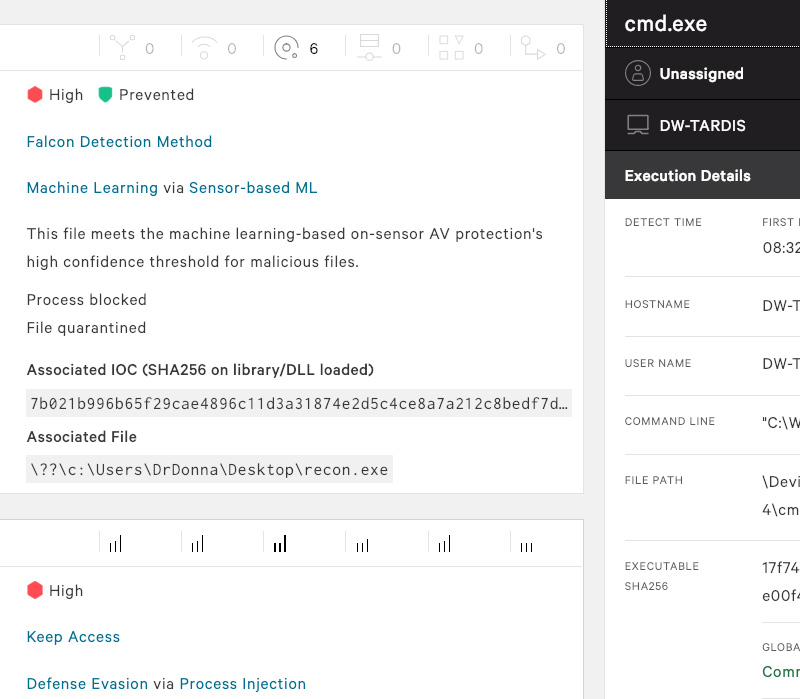
CrowdStrike Falcon® IntelligenceThreat Intelligence
-
FALCON
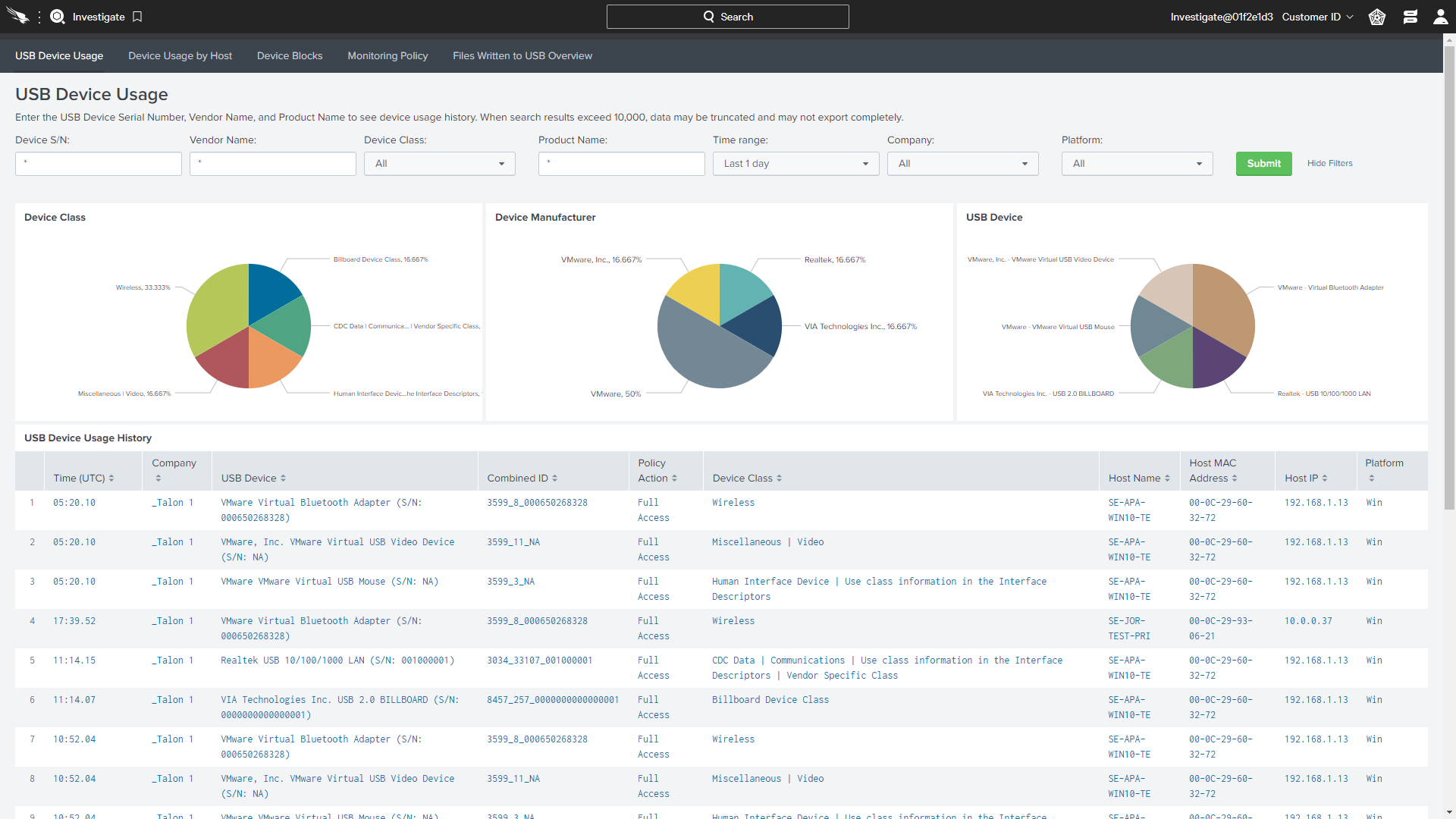
Device ControlUSB Device Control -
Falcon Firewall Management Host Firewall Control
-
FALCON
INSIGHTEndpoint Detection
& Response -
FALCON
OVERWATCHThreat Hunting -
FALCON
DISCOVERIT Hygiene -
FALCON IDENTITY
PROTECTIONIntegrated Identity Security -
CROWDSTRIKE
SERVICESIncident Response &
Proactive Services
- Falcon Pro Replace legacy AV with market-leading NGAV and integrated threat intelligence and immediate response
-
Available with
FALCON ENTERPRISE
AND FALCON ELITE -
Available with
FALCON ENTERPRISE
AND FALCON ELITE -
Available with
FALCON ELITE -
Available with
FALCON ELITE - Learn more about CrowdStrike Services
Flexible Bundles:
Included Component
Elective Component

Recognized by Gartner Peer Insights CrowdStrike named a Customers’ Choice vendor in the 2021 Gartner Peer Insights Report for EPP. Learn More
NEXT-GEN AV SOLUTION:
ENDPOINT PROTECTION PRO
Falcon Endpoint Protection Pro offers the ideal AV replacement solution by combining the most effective prevention technologies and full attack visibility with built-in threat intelligence — all in a single lightweight agent.
BUSINESS VALUE
-
Boost Prevention
Capabilities -
Increases Security
Efficiency -
Increases Endpoint
Performance -
Eliminate Cost and
Burden Associated with
Keeping Up-to-date
We don’t have an antivirus solution that’s waiting on signatures to be developed and pushed out. What we’ve got is that we’re part of a larger collection of organizations that are running CrowdStrike, so any data that we see gets fed back into the system and someone else will benefit from that knowledge. And it’s all because it is cloud-based.

MODULES INCLUDE
INTERESTED?
A CrowdStrike security expert is standing by to offer information, advice, or help with your purchase.
request info